When to Use Secrets
Use a secret whenever you’re working with:- API keys (e.g. OpenWeather, Slack, Notion)
- Authorization tokens
- Other sensitive config values you don’t want exposed in your agent steps
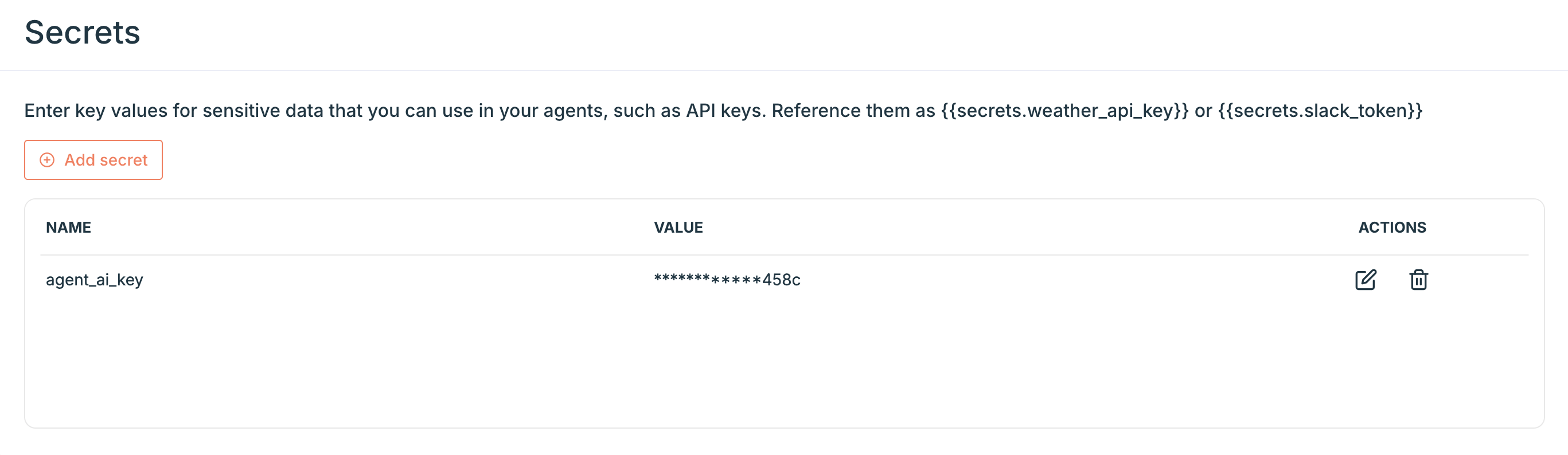
How to Add a Secret
To add a new secret:- Go to the Secrets tab from the profile navigation menu.
- Click Add secret
- Enter a name (e.g. weather_api_key) and the secret value
- Click Save
How to Use a Secret in an Agent
Anywhere you’d normally paste an API key or token in a REST call or prompt, use the secret reference format:Best Practices
- Use clear, descriptive names (e.g.
notion_token,slack_webhook) - Avoid including the actual key in prompt text or test runs
- Rotate or update secrets as needed in the Secrets tab without having to update your agents

